For many developers and system administrators, upgrading PHP is a routine and necessary task. However, sometimes even a small PHP version upgrade can cause unexpected issues—especially when it involves secure communications like sending emails via SMTP with TLS encryption. That’s exactly what happened when a widely used web application suddenly failed to send emails securely after a PHP upgrade.
TLDR: After a PHP upgrade, SMTP email sends over TLS started failing due to deprecated or incompatible TLS settings. The issue was traced back to PHP’s use of the underlying OpenSSL library and stricter enforcement of security protocols. Restoring email functionality involved configuring proper SSL context options and making email libraries TLS-compatibility aware. The final fix ensured secure SMTP sends and compatibility with modern email servers.
What Went Wrong After the PHP Upgrade?
Email communication in web applications is often handled through SMTP, usually wrapped in a secure transmission layer like TLS. Modern PHP applications use libraries such as PHPMailer, SwiftMailer, or Symfony Mailer to interact with SMTP servers securely. These libraries rely on PHP’s built-in stream functionality and, by extension, OpenSSL for secure transmission.
After upgrading from PHP 7.4 to PHP 8.1, developers began noticing failures in email delivery. Here’s what they encountered:
- Timeouts during SMTP handshake.
- SSL errors such as “stream_socket_enable_crypto(): SSL operation failed.”
- Incompatibility with older SMTP server configurations.
This was particularly puzzling since nothing in the mail-sending code had changed. Mail configurations were intact, SSL certificates were valid, but messages would no longer send—especially when using services like Gmail, Office365, and custom SMTP providers.
Understanding the Root Cause
The culprit turned out to be changes in how PHP 8.0+ integrates with OpenSSL. Specifically:
- PHP began defaulting to stricter TLS requirements.
- Weak protocols like TLS 1.0 and 1.1 were deprecated and even disabled by default in the underlying OpenSSL library.
- Some email servers (especially older ones or misconfigured ones) still attempted to negotiate these older protocols, leading to connection failures.
What amplified the problem was that most PHP mailing libraries weren’t explicitly setting which TLS version or stream options to use—previously relying on the default “auto negotiate” feature, which had now changed behavior.
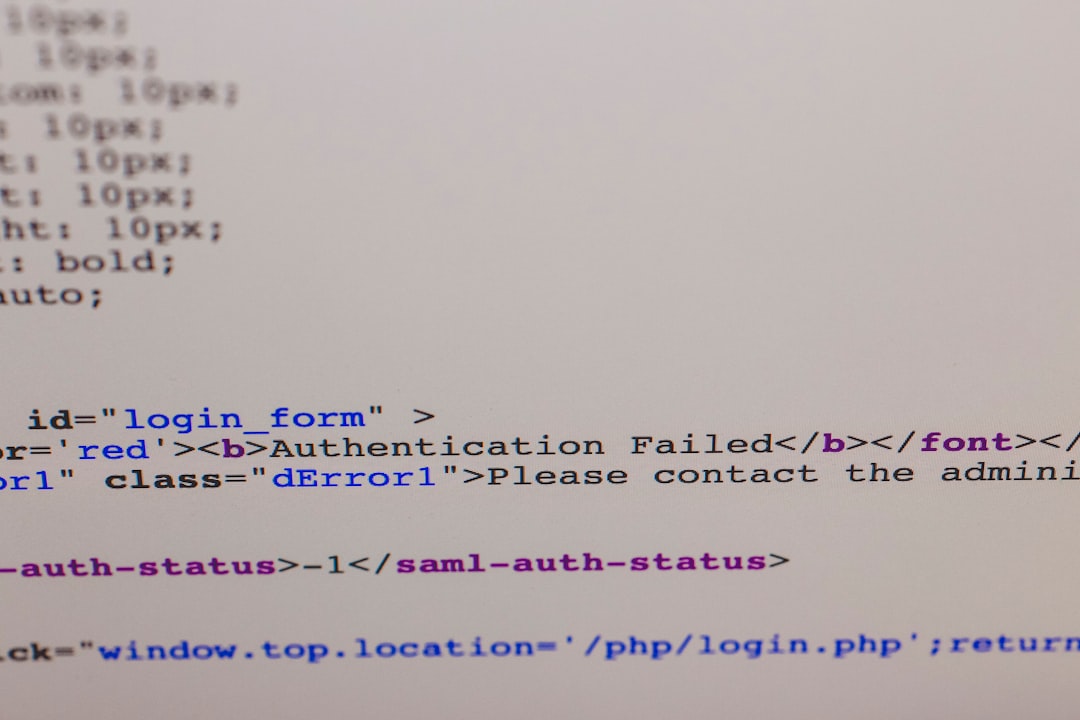
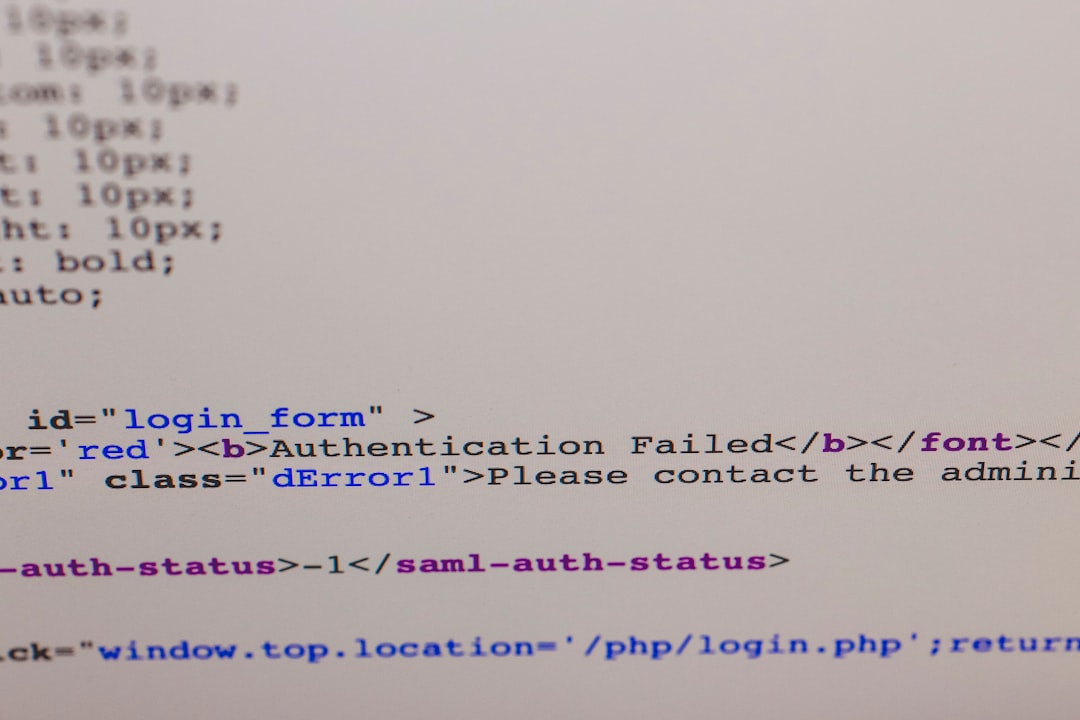
Real-World Example of the Error
stream_socket_enable_crypto(): SSL operation failed with code 1.
OpenSSL Error messages:
error:14094416:SSL routines:ssl3_read_bytes:sslv3 alert certificate unknownThis message indicates that the TLS handshake failed due to incompatibilities between the client (your app) and the server (SMTP provider). Often the solution is not on the server side, but in how the PHP stream and SSL context are set up in your code.
The TLS Compatibility Fix
The fix involved updating the email sending code to explicitly define the stream context and supported TLS/SSL versions. Here’s how the compatibility was restored:
1. Specifying SSL Context Options
When initializing the mailer, a specific set of SSL options were passed, making the transport layer compatibility explicit:
$contextOptions = stream_context_create([
'ssl' => [
'verify_peer' => true,
'verify_peer_name' => true,
'allow_self_signed' => false,
'crypto_method' => STREAM_CRYPTO_METHOD_TLS_CLIENT,
]
]);
$mailer->setStreamContext($contextOptions);This ensured only secure and compatible TLS methods like TLS 1.2 and 1.3 were requested during the handshake.
2. Upgrading the Mail Library
Older versions of libraries like PHPMailer or SwiftMailer may not be compatible with modern TLS requirements. Upgrading to the latest releases (post PHP 8 support) fixes many issues:
- PHPMailer: Ensure version 6.5 or above.
- SwiftMailer: Deprecated in favor of Symfony Mailer; consider switching for long-term support.
- Symfony Mailer: Fully PHP 8+ and TLS 1.3 compliant.
3. TLS Port and Encryption Mode Awareness
Ensure you are using SMTP encryption modes correctly:
- Port 587 with STARTTLS (modern default).
- Port 465 with SMTPS should be used only when STARTTLS is not available.
Libraries must know whether to enable encryption immediately (for port 465) or negotiate it after connecting (for 587). Mismatches here result in instant TLS failures.
Diagnosing With Verbose Debug Output
Adding verbose debug logs can help pinpoint the error in the SMTP session:
$mailer->SMTPDebug = 2;
$mailer->Debugoutput = 'html';This displays every communication detail between client and server, revealing whether TLS negotiation is failing, timing out, or failing certification.
What Changed In Your PHP?
Some key things that changed during the PHP upgrade:
- Default SSL/TLS behavior: Stricter enforcement, disabled TLS 1.0/1.1.
- OpenSSL versions: Upgrading PHP may also upgrade linked OpenSSL libraries.
- Deprecation warnings: Use of legacy settings now often throws visible errors.
It’s essential after any PHP upgrade to check your underlying library versions using:
php -i | grep OpenSSLThis reveals what version of OpenSSL PHP is using—critical for TLS compatibility.
Guidelines for Preventing Future SMTP TLS Issues
To future-proof your application and avoid TLS issues on future upgrades:
- Regularly update your mail libraries—many adapt to changes in PHP and TLS over time.
- Test upgrades in staging environments with full mail-sending functionality.
- Use proper stream context options and test against multiple SMTP providers.
- Avoid self-signed certificates unless absolutely necessary, and never in production.
Lessons Learned
The surprise failure of SMTP sends after a PHP upgrade is a reminder that “invisible” dependencies like OpenSSL can affect core application behavior. Implicit settings that worked in older versions may not be secure or allowed in newer environments. Proactively configuring context options and keeping libraries updated is essential for robust, secure email communications.
Security and email deliverability are tightly intertwined with protocol compatibility. TLS is critical for data privacy, but even small incompatibilities can result in dropped messages—silently killing app features like password resets, registration confirmations, or login alerts.
Conclusion
Upgrading PHP should make your application more secure, not break it. When it comes to using SMTP over TLS, ensuring compatibility with your mailer library, PHP’s stream context, and the latest TLS protocols is key. A simple PHP upgrade may expose hidden technical debt, but also creates an opportunity to make your system more robust and modern. By understanding the changes and proactively applying fixes, your application can regain its ability to send emails securely—and reliably.
Always remember: if your app relies on sending critical emails, make SMTP and TLS testing a key part of your QA process. Don’t let a silent TLS failure become a customer service emergency.